Hexordia Weekly CTF Challenge 2024 - Week 4 Writeup
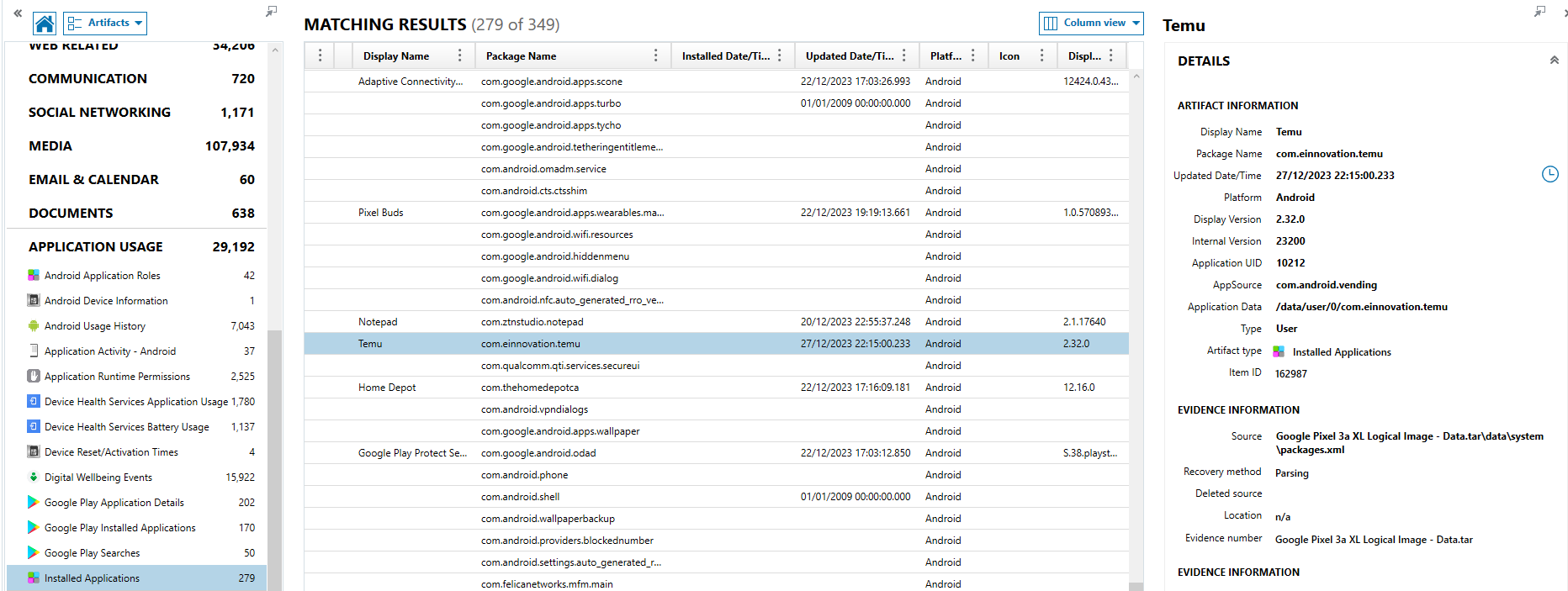
Android - TEaM U prep (15 points) What item that Rocco was shopping for came back in stock? From the capitalized letters in the challenge " TE a M U prep", it suggested that we probably should look into the direction of Temu, a Chinese online marketplace app. The Temu app was also installed on the Android device: The item that Rocco was shopping was likely browsed by Rocco in app or even added into shopping cart at some point. Following this direction, the Temu app SQLite databases from /data/data/com.einnovation.temu/databases directory have been checked one by one. One of the SQLite databases " ChatDB_BCM6G5ASA5K73AN2N7S3TQYUS2MOBTVG2RFRUULJ_msgbox_2.db " contained some in-app messages that were pushed to Rocco. There was a summary text of " Almost sold out " from summary column where id = " 10000010 ''. The relevant info column appeared to have contained a JSON object: If this JSON object was sorted and beautified in NotePad++, it ...